CVE-2024-1709 - ConnectWise ScreenConnect - Authentication Bypass to RCE
ConnectWise ScreenConnect is a remote support and remote access software solution that allows users to securely connect to and control devices from anywhere. It comes as a cloud service or as an on-premise solution that can be installed and managed by customers on their own servers.
On February 19, 2024 ConnectWise disclosed 2 vulnerabilities affecting on-premise ScreenConnect versions 23.9.7 and earlier:
- CVE-2024-1709 - Authentication Bypass vulnerability
- CVE-2024-1708 - Path Traversal vulnerability
Cloud versions were also vulnerable but were patched by ConnectWise prior to the disclosure of vulnerabilities.
Vulnerability Overview
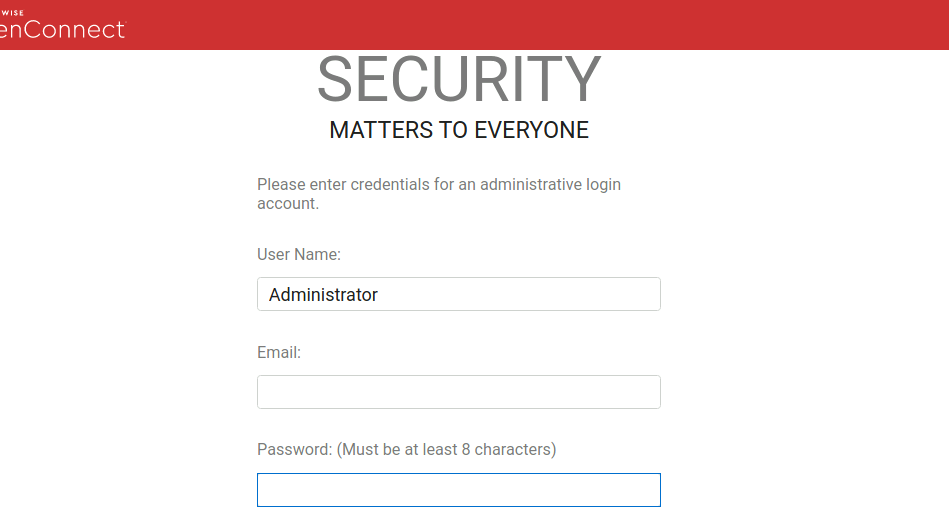
After the installation, on-premise ScreenConnect requires you to perform the initial configuration via the web interface (SetupWizard.aspx endpoint). Once the initial configuration is done, that endpoint is supposed to be inaccessible. There is a check that redirects all requests to the login page. The check works by comparing the Request.Path to SetupWizard.aspx.
Researchers discovered that if the adversary adds / followed by any set of alphanumerical characters after SetupWizard.aspx (for ex, SetupWizard.aspx/something), redirect will fail and they will be able to access the setup wizard.
Per Huntress analysis this happens due to the .Net internal workings. .Net allows passing URL path components to applications by adding them to the end of the mapped legitimate URLs (for ex, SetupWizard.aspx/something). The problem is, Request.Path contains both the URL and components. As SetupWizard.aspx/something no longer matches the expected SetupWizard.aspx, the check fails and the adversary is allowed to access the setup wizard.
The second step in the setup wizard is the admin user creation.
The main problem here is that the new admin user is created immediately, after the form is submitted, without the need of completing the configuration process. As soon as the form is submitted, all other local users are also dropped.
Upon successful exploitation, an unauthenticated adversary is able to gain administrator level access to an already configured ScreenConnect instance by replacing the administrator credentials.
Authentication Bypass to RCE
Adversaries can achieve remote code execution by chaining CVE-2024-1709 and CVE-2024-1708 or by using ScreenConnect’s Extensions functionality. Both of these methods require admin access which is already gained via CVE-2024-1709. There are multiple exploit scripts and a Metasploit module available on the internet.
Remediation
For on-premise installations, vulnerability was fixed on version 23.9.8. The cloud solutions were patched by ConnectWise on February 15, 2024 prior to the disclosure of the vulnerability.
Considering the severity of the vulnerability and ease of exploitation, customers are advised to patch their instances as soon as possible. Furthermore, an investigation should be conducted to determine if and how far their systems have been compromised. Apart from patching and their hardening guidelines, ConnectWise also advices customers to follow the ScreenConnect Remediation and Hardening Guide by Mandiant. The Mandiant guide will especially be useful for the customers that have been exploited.
Sources
- NIST NVD - CVE-2024-1709
- NIST NVD - CVE-2024-1708
- Understanding the ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708) by Huntress
- Security Bulletin regarding the vulnerabilities by ConnectWise
- Responding to the ScreenConnect Vulnerability by ConnectWise
- ScreenConnect Remediation and Hardening Guide by Mandiant